Water cooling
Water cooling is a method of heat removal from components. As opposed to air cooling, water is used as the heat transmitter. Water cooling is commonly used for cooling internal combustion engines in automobiles machine guns, cooling of lubricant oil in pumps; for cooling purposes in heat exchangers; cooling products from tanks or columns, and recently, cooling of various major components inside high-end personal computers. The main mechanism for water cooling is convective heat transfer. and large electrical generators.
Advantages
The advantages of using water cooling over air cooling include water's higher specific heat capacity, density, and thermal conductivity. This allows water to transmit heat over greater distances with much less volumetric flow and reduced temperature difference.
For cooling CPU cores its primary advantage is that its tremendously increased ability to transport heat away from source to a secondary cooling surface allows for large, more optimally designed radiators rather than small, inefficient fins mounted directly on the heat source.
The "water jacket" around an engine is also very effective at deadening mechanical noises, which makes the engine quieter. However, the primary disadvantage is that it costs significantly more than an air cooled engine system.
 Pressurization
Pressurization
Modern automotive cooling systems are slightly pressurized. This raises the boiling-point of the coolant and reduces evaporation.
Antifreeze
The use of water cooling carries the risk of damage from freezing. Automotive and many other engine cooling applications require the use of a water and antifreeze mixture to lower the freezing point to a temperature unlikely to be experienced. Antifreeze also inhibits corrosion from dissimilar metals and can increase the boiling point, allowing a wider range of water cooling temperatures. Its distinctive odor also alerts operators to cooling system leaks and problems that would go unnoticed in a water-only cooling system. The heated water can also be used to warm the air conditioning system inside the car, if so desired.

Other additives
Other less common chemical additives are products to reduce surface tension. These additives are meant to increase the efficiency of automotive cooling systems. Such products are used to enhance the cooling of underperforming or undersized cooling systems or in racing where the weight of a larger cooling system could be a disadvantage.
Video
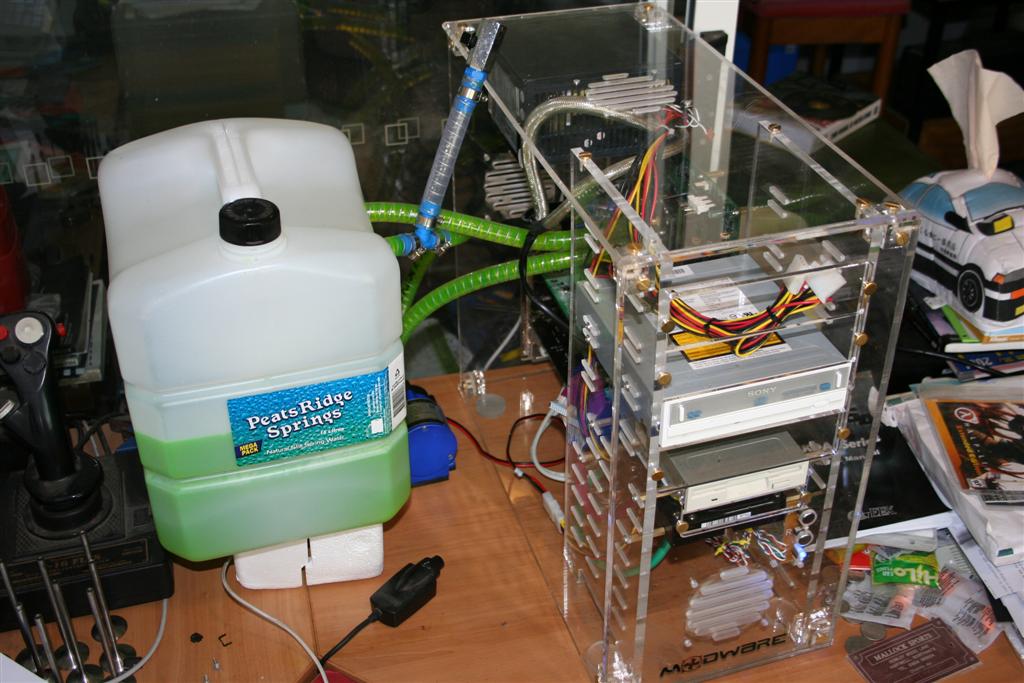
Computer usage
In the past few years, water cooling is being realized for cooling computer components, especially the CPU. Water cooling usually consists of a CPU water block, a water pump, and a heat exchanger (usually a radiator overclocking, but with improved heat handling capabilities hotter processors can be supported. Less commonly, GPUs, Northbridges, hard drives, memory, VRM, and even power supplies are water cooled. with a fan attached). Water cooling not only allows for quieter operation and improved
Water coolers for computers (other than mainframes) were, up until the end of the '90s, homemade. They were put together using car radiators (or more commonly, a car's heater core), aquarium pumps and home made water blocks. In conjunction with these automotive items users would pair laboratory-grade PVC and Silicone tubing and various reservoirs (home made using plastic bottles, or constructed using cylindrical acrylic or sheets of acrylic, usually clear) and or a T-Line. More recently a growing number of companies are manufacturing pre-made, specialised components, allowing water cooling to be compact enough to fit inside a computer case. This, coupled with the growing amount of heat coming from the CPU has greatly increased the popularity of water cooling. However, it is still a very niche market.
Dedicated overclockers will occasionally use vapor-compression refrigeration or thermoelectric coolers in place of more common standard heat exchangers. Water cooling systems in which water is cooled directly by the evaporator coil of a phase change system are able to chill the circulating coolant below the ambient air temperature (an impossible feat using a standard heat exchanger) and, as a result, generally provide superior cooling of the computer's heat-generating components. The downside of phase-change or thermoelectric cooling is that it uses much more electricity and antifreeze must be added due to the low temperature. Additionally, insulation, usually in the form of lagging around water pipes and neoprene pads around the components to be cooled, must be used in order to prevent damage caused by condensation of water vapour from the air on the surfaces at below ambient temperature. Common places from which to borrow the required phase change systems are a household dehumidifier or air conditioner.
An alternative cooling system, which enables components to be cooled below the ambient temperature, but which obviates the requirement for antifreeze and lagged pipes, is to place a thermoelectric device (commonly referred to as a 'Peltier junction' or 'pelt' after Jean Peltier, who documented the effect) between the heat-generating component and the water block. Because the only sub-ambient temperature zone now is at the interface with the heat-generating component itself, insulation is required only in that localized area. The disadvantage to such a system is that pelts typically draw a large amount of power, and the water cooling system is required to remove this power, in addition to the heat generated by the component. Another possible danger is condensation, resulting from the ambient air right around the pelt being cold. This condensation could cause a short-circuit, shutting the computer down or possibly permanent damage. A proper installation requires that the Peltier be "potted" with silicone epoxy. The epoxy is applied around the edges of the device, preventing air from entering or leaving the interior.
Apple's Power Mac G5 was the first mainstream desktop computer to have water cooling as standard, and Dell later followed suit by shipping their XPS computers with liquid cooling
, using thermoelectric cooling to help cool the liquid. Currently, Dell's only computers to offer liquid cooling are their Alienware desktops.

Industrial usage
Most industrial cooling towers use river water or well water as their source of fresh cooling water. The large mechanical induced-draft or forced-draft cooling towers in industrial plants such as power stations, petroleum oil refineries, petrochemical plants and natural gas processing plants continuously circulate cooling water through heat exchangers and other equipment where the water absorbs heat. That heat is then rejected to the atmosphere by the partial evaporation of the water in cooling towers where upflowing air is contacted with the circulating downflow of water. The loss of evaporated water into the air exhausted to the atmosphere is replaced by "make-up" fresh river water or fresh cooling water. Since the evaporation of pure water is replaced by make-up water containing carbonates and other dissolved salts, a portion of the circulating water is also continuously discarded as "blowdown" water to prevent the excessive build-up of salts in the circulating water.
High grade industrial water (produced by reverse osmosis) and potable water is sometimes used in industrial plants requiring high-purity cooling water.
Some nuclear reactors use heavy water as cooling. Heavy water is employed in nuclear reactors because it is a weaker moderator of the nuclear chain reaction. This allows for the reactor core size to be smaller, or for the use of less enriched fuel. For the main cooling system, normal water is preferably employed through the use of a heat exchanger as heavy water is much more expensive. Reactors that use other materials for moderation (graphite) may also use normal water for cooling.

Environmental impacts
On very large rivers, but more often at coastal and estuarine sites, "direct cooled" systems are often used instead. These industrial plants do not use cooling towers and the atmosphere as a heat sink but put the waste heat to the river or coastal water instead. These once-through cooling (OTC) systems thus rely upon a good supply of river water or sea water for their cooling needs. The warmed water is returned directly to the aquatic environment, often at temperatures significantly above the ambient receiving water. Thermal pollutionbiocide to prevent fouling in heat exchangerscondensers and other equipment, but in some instances such control can be exercised instead through frequent cleaning, antifouling paints (both toxic-release and non-toxic), or heat treatment. of rivers, estuaries and coastal waters is an issue which needs to be addressed when considering the siting of such plants. Other impacts include "impingement" (the capture of larger organisms such as fish and shrimp on screens protecting the small bore tubes of the heat exchangers from blockage) and "entrainment" (the combined effects of temperature, pressure, biocide residual and turbulence/shear on smaller organisms entrained with the cooling water and then expelled back to the aquatic environment in the effluent). The cooling water in such heat exchange cycles is often treated with a like.




.jpg)

.jpg)
.jpg)
.jpg)
.jpg)
.jpg)
.jpg)
.jpg)
.jpg)

















